Compliance & Certifications
SteamIQ is built for industrial environments where safety, reliability, and regulatory compliance aren’t optional—they’re mission-critical.
Our monitors meet international safety, communication, and industry-specific standards, ensuring they’re ready for deployment in even the most demanding facilities.
UL certified – UL61010-1
CE Marked – Complies with European safety regulations
FCC & IC Approved – Meets US & Canadian wireless standards
IP67 rated
Worldwide LoRa frequency plans available (US915, EU868, AU915)
US Patents 10,620,170, 11,016,063, 12,276,638
CA Patent 3,074,672

Downloadable Documents
Access all essential documentation
Installation Manual
Install with ease—no wiring, no prior experience required.
Our step-by-step manual walks you through mounting and setup using basic tools in just minutes.
API Documentation
SteamIQ offers a secure API for seamless integration with your building management system (BMS), cloud platform, or analytics stack.
Access real-time steam trap data, alarm states, and historical insights directly through our developer-ready API documentation.
Datasheet
Our datasheet covers dimensions, specs, battery life, mounting options, and more in one easy-to-reference PDF.
Our monitors meet international safety, communication, and industry-specific standards, ensuring they’re ready for deployment in even the most demanding facilities.
LoRaWAN System architecture
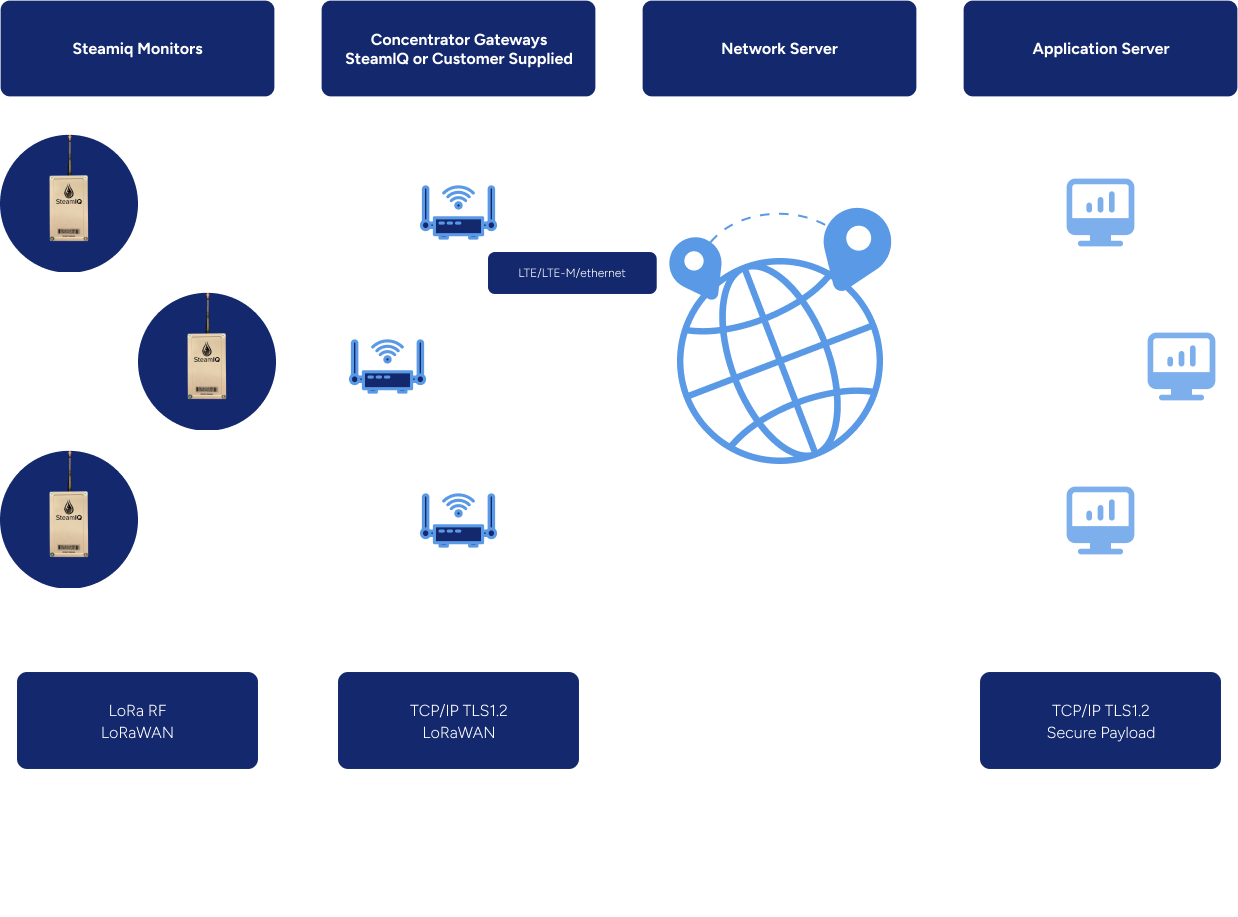
Network FAQ
Yes, SteamIQ supports customer-owned LoRaWAN networks.
We provide a standard KEYS file (DevEUI, AppEUI, AppKey) for onboarding to your LoRa network server. Uplink data is forwarded to our cloud via HTTPS webhook integration. SteamIQ is already integrated with leading network providers including Actility, Senet, Everynet, Loriot, TTN, and Kore. For advanced routing, payload decoding, or backend configuration support, contact us—we’re happy to assist.
While range depends on site conditions, SteamIQ monitors are proven to punch through multiple concrete floors and dense industrial infrastructure. Built on LoRaWAN, they’ve been deployed in some of the harshest environments—from the oilfields of Texas to the Alberta oilsands. LoRa networks are also easy to scale—simply add gateways to increase coverage, range, and redundancy. SteamIQ offers the longest wireless range of any steam trap monitor available.
While LoRaWAN gateways don’t require direct line of sight, elevation significantly improves coverage. We recommend placing gateways as high as possible—on roofs, pipe racks, or elevated platforms within the facility.
SteamIQ’s gateway package includes a PoE injector that supports up to 300 feet of CAT5 cable between the power supply and the gateway, allowing flexible installation even where 120–240V AC power isn’t available. We’ve even deployed fully solar-powered gateways in remote or off-grid locations. Wherever your traps are, we’ll get coverage there.
Gateways can use either Ethernet or cellular backhaul to transmit data. Most customers prefer cellular, which keeps the monitoring network completely separate from the facility’s IT infrastructure. Gateways should be installed where reliable cellular signal is available, and SteamIQ supports deployments worldwide through access to global cellular networks.
LoRaWAN uses built-in, end-to-end security. All data is encrypted at the device level using AES-128 encryption and remains encrypted through transmission to the LoRa Network Server (LNS). From there, data is securely forwarded to SteamIQ’s cloud platform via HTTPS (TLS), ensuring encryption in transit and at rest.
Yes. SteamIQ supports integration with customer-owned platforms including BMS systems, cloud environments, data lakes, and historians. While the dashboard can function as a standalone interface, integration enables centralized visibility and deeper analytics.
Data access is provided through a secure API, with documentation available here for implementation guidance. Packet decoding and custom routing support are also available upon request.
Yes. SteamIQ supports flexible deployment models that can align with enterprise information security standards. Contact us to review your requirements—we’re happy to assist with documentation, network architecture planning, and integration options to meet internal security policies.